National security cutter Bertholf, EADS HC-144, and H-65 helicopter
The US Coast Guard (USCG) received $10 billion for fiscal year (FY) 2015, $435.9 million above the Obama Administration’s FY 2015 budget request. The FY 2015 budget, in conjunction with the newly released Navy maritime strategy, A Cooperative Strategy for 21st Century Seapower, provides insight towards future USCG priorities, procurement programs, and sought after capabilities and technologies.
The new maritime strategy outlined broad Navy priorities since the release of the earlier 2007 edition. At the Department of the Navy level, the new maritime strategy indicates that the service will place a greater emphasis on all domain access, the ability to operate in contested environments on the surface, undersea, space, cyber, electromagnetic spectrum, etc. The Navy’s decision to prioritize all domain access, so that it is nearly equivalent to the Navy’s nuclear deterrence mission, is a response to anti-access area denial threats from China and Russia (Freedberg, 2015). The document also emphasizes the role of electronic warfare, cyber warfare, working with US allies, and increasing the Navy’s forward presence in the Indo-Asia-Pacific and the Middle East.
At the USCG level, the document indicated the Coast Guard would prioritize the development of the service’s cyber defense capabilities, and allocate additional resources towards the Western Hemisphere as well as the Arctic and the Antarctic. The USCG will release its first cyber security strategy next month, which will underscore the importance of protecting the nation’s heavily automated ports, establish situational awareness to cyber events, and protect USCG assets (Watkins, 2015). Rear Admiral Peter Brown, Assistant Commandant for Response Policy recently underscored the need for the USCG to embrace its new cyber security role:
“So many aspects of maritime transportation are now reliant on computer controls — not only the more traditional navigation and communications technology but also the physical responses of facilities and vessels such as unmanned systems that unload and scan cargo containers…We have to make sure from a Coast Guard perspective that the supply chain is secure from a cyber-perspective. The Coast Guard needs to be aware of what threats and challenges are out there to the global maritime transportation system through cyber access”
In terms of geographic priorities, commandant Zukunft explained the shift of resources to the Western Hemisphere is in response to the rising level of violence in Central and South America (Grady, 2015). Zukunft explained the influx of unaccompanied children from Latin America to the US border in the summer of 2014, in addition to the ongoing demand for counter narcotic missions, had an impact on the service’s decision to base more resources in the Western Hemisphere. Zukunft justified the increased resources dedicated to both the Arctic and Antarctic as a result of rising international maritime activity in both areas. The Artic in particular is likely to receive more resources as a result of significantly increased Russian activity in the region, following the seizure of Crimea and the ongoing territorial disputes between Russia, Canada, and Denmark. In order to facilitate the increased demand for the USCG in both the Western Hemisphere and the Artic, the FY 2015 budget provides billions for new systems and platforms.
ScanEagle unmanned aerial system (UAS) launching from the USCG cutter Bertholf
The FY 2015 budget would also fund the purchase of additional frigate-sized national security cutters, HC-130J maritime surveillance and transport aircraft, H-60 helicopters, and continue the development of both the polar icebreaker and icebreaker tugs. The USCG is also experimenting in deploying UAS from its fleet of cutters and icebreakers. The Boeing Insitu ScanEagle shown above is expected to be procured in the Coast Guard’s FY 2016 budget, with deployments beginning in FY 2017 following successful ship based tests and sea trials (Rico, 2013). The USCG also tested the AeroVironment RQ-20 Puma in August 2014; the RQ-20 flew from the USCGC Healy icebreaker operating in the Arctic (Smith, 2014). The deployment of UAS from both cutters and icebreakers would greatly enhance the USCG’s maritime surveillance and intelligence surveillance and reconnaissance capabilities.
The USCG is in the midst of a transformational process to prioritize the Western Hemisphere, the Arctic, and significantly augment its cyber defense capabilities. Procurement priorities over the next few years will focus on the modernization of its fleet of national security cutters, gaining extended maritime surveillance capabilities via UAS, and developing new icebreakers to maintain the United States’ presence in the Arctic. However, the continuation of sequestration into FY 2016 will constrain the USCG’s ability to field a more modern fleet of cutters, as well as other comparatively expensive platforms such as icebreakers.
Sources
- Coast Guard cyber plan to focus on ports, shipping, Steve Watkins, 2015.
http://www.federaltimes.com/story/government/cybersecurity/2015/03/12/coast-guard-cyber-plan-ports-shipping/70203712/ - Committee Releases Fiscal Year 2015 Homeland Security Appropriations Bill, 2015.
http://appropriations.house.gov/news/documentsingle.aspx?DocumentID=393930 - Winning The War Of Electrons: Inside The New Maritime Strategy, Sydney J. Freedberg, Jr., 2015.
http://breakingdefense.com/2015/03/winning-the-war-of-electrons-inside-the-new-maritime-strategy/ - Boats, Biometrics and Other Items in the Homeland Security Funding Bill, Eric Katz, 2015.
http://www.defenseone.com/politics/2015/03/boats-biometrics-and-other-items-homeland-security-funding-bill/106806/?oref=search_DHS - House OKs Controversial DHS Funding Measure, John T. Bennett, 2015.
http://www.defensenews.com/story/defense/policy-budget/congress/2015/01/14/homeland-security-dhs-immigration-house/21752693/ - UAV a success for Coast Guard in major drug bust, Antonieta Rico, 2013.
http://www.militarytimes.com/article/20130810/NEWS03/308100005/UAV-success-Coast-Guard-major-drug-bust - Coast Guard Icebreaker Launches, Lands First Arctic Drone, Matthew F. Smith, 2014.
http://www.knom.org/wp/blog/2014/08/31/coast-guard-icebreaker-launches-lands-first-arctic-drone/ - Maritime Security: Sneak Preview of the Coast Guard’s Cybersecurity Strategy, Lt. Jodie Knox, 2015.
http://inhomelandsecurity.com/maritime-security-sneak-preview-of-the-coast-guards-cybersecurity-strategy/ - Coast Guard Information Technology, Sensor Needs Go Unfilled, Stew Magnuson, 2014.
http://www.nationaldefensemagazine.org/archive/2014/December/Pages/CoastGuardInformationTechnologySensorNeedsGoUnfilled.aspx - Coast Guard Closer to Acquiring Ship-Based Drones, Stew Magnuson, 2014.
http://www.nationaldefensemagazine.org/archive/2014/July/Pages/CoastGuardClosertoAcquiringShip-BasedDrones.aspx - Cyber and Electronic Warfare Stand Out in Navys Maritime Strategy, Kris Osborn, 2015.
http://www.military.com/daily-news/2015/03/13/cyber-and-electronic-warfare-stand-out-in-navys-maritime.html
Developments in DHS: Part I – Improving Border Security
In early March, Congress passed a $39.7 billion budget for the Department of Homeland Security (DHS) which is $400 million dollars greater than the enacted FY 2014 levels. Most components of DHS received a funding increase, but the FY 2015 budget prioritizes a series of initiatives to strengthen border security through hiring new personnel, developing new biometric identification technologies, and supporting previous efforts to improve border infrastructure. Part II of this series on the FY 2015 DHS budget will detail significant increases in the capability of the Coast Guard as a result of the FY 2015 budget, as well as trends within the agency.
CBP MQ-9 “Reaper” UAV
Immigration Customs and Enforcement (ICE) received a disproportionately large increase in funding relative to other DHS components at $944 million, a 13% increase, which is 16% greater than the figure originally requested by the Obama Administration. ICE will spend $62 million this year to hire new support staff and agents to counter human trafficking and drug smuggling operations (Katz, 2015). US Customs and Border Protection (CBP) received a roughly 1% increase in funding, but is also expected to make significant increases to its personnel. The FY 2015 budget funds 23,775 CBP officers and 21,370 border patrol agents. CBP is also expanding its investment into its biometric identification system called IDENT.
IDENT currently contains the finger prints and facial images of more than 170 million foreigners, as well as 600,000 iris templates (Sternstein, 2015). Planned upgrades to IDENT will enable CBP to match more than 10 million iris and facial images through an expansion of IDENT infrastructure. While the IDENT upgrades are expected to improve the system’s identification capabilities, the system is expected to have difficulty in compensating for changes to the iris over time,
“Iris matching is by no means 100 percent accurate. The texture of an individual’s iris changes with aging — though by how much is controversial, and engineers have demonstrated that ID thieves can hack iris template databases to duplicate other people’s eye patterns. ‘We’re trying to get enough knowledge right now on how to do iris [scans] to be able to actually process the images we’ve been collecting for a couple of years now,’ Fritzsche [director of identify technology at DHS Office of Biometric Identity Management] said during public remarks. ‘That’s what we’re doing with this pilot.’” – Aliya Sternstein, 2015
The FY 2015 DHS budget also funds a biometric exit mobile application under CBP as well as 95,000 flight hours of border surveillance; CBP operates a small fleet of MQ-9 unmanned aerial vehicles (Katz, 2015).
In conjunction with the Canadian Border Service Agency, the Department of Transportation, and Transport Canada, CBP completed a series of border infrastructure projects under the Border Infrastructure Investment Plan (BIIP) I and II, which were completed in 2014. BIIP 1.0 upgraded the infrastructure in seven key Canada-US border sites, and BIIP 2.0 expanded the program to include the top 20 crossings by two-way trade, 25 major ports and the top 15 crossings based on two-way non-commercial traffic volume (Transport Canada, 2014). BIIP 2.0 includes investments in intelligent transportation systems such as wait time measurement technology, advanced traveler information systems, and traffic management centers. Cumulatively, BIIP 1.0 and 2.0 will improve security, reduce wait times, and improve the reliability of shipments.
In summary, DHS is in the process of making significant additions to border security through new technologies, upgraded border infrastructure, and additional personnel. However, boosting border security does not come without a cost: the Transportation Security Administration will face a $94.3 million reduction in its budget, as well as a cap on airport screening personnel (Medici, 2015). Furthermore, DHS’ FY 2015 budget request reduced funding for the Science and Technology directorate by nearly 10% when compared to the enacted FY 2014 budget. The prioritization of border security and the development of biometric identification technologies reflects shifting agency priorities. Cyber security is also receiving increased attention within DHS as shown by the creation of the new National Cybersecurity and Communications Integration Center and developments within the Coast Guard which will be discussed in Part II.
Sources
- Budget in Brief FY 2015, Department of Homeland Security, 2015.
http://www.dhs.gov/sites/default/files/publications/FY15BIB.pdf - Shutdown averted: Congress funds DHS through 2015, Andy Medici, 2015.
http://www.federaltimes.com/story/government/dhs/management/2015/03/03/dhs-shutdown/24323381/ - Homeland Security To Roll Out Biometrics Along the Border This Summer, -Aliya Sternstein, 2015
http://www.defenseone.com/technology/2015/01/homeland-security-roll-out-biometrics-along-border-summer/103968/?oref=search_DHS - Boats, Biometrics and Other Items in the Homeland Security Funding Bill, Eric Katz, 2015.
http://www.defenseone.com/politics/2015/03/boats-biometrics-and-other-items-homeland-security-funding-bill/106806/?oref=search_DHS - Congress narrowly averts DHS shutdown, Andy Medici, 2015.
http://www.federaltimes.com/story/government/dhs/management/2015/02/27/dhs-shutdown/24158055/ - Border Infrastructure Investment Plan Canada – United States December 2014
- Borders, Transport Canada, 2015.
http://www.tc.gc.ca/eng/policy/acg-acgd-menu-borders-2144.htm
Upcoming UAS Regulations
DJI Phantom-1 sUAS
The Federal Aviation Administration (FAA) is looking to overhaul laws pertaining to the use of small unmanned aerial systems (sUAS), classified as aircraft weighing less than 55 pounds, within the next year. The released Notice of Proposed Rulemaking (NPRM) stipulates measures relating to the operation of non-recreational sUAS in terms of height restrictions, aircraft registration, daytime flight restrictions, operator certification, and line of sight restrictions. The NPRM first step in what is likely to be a yearlong process before enforcement of new regulations begins. The White House Office of Information and Regulatory Affairs, within the Office of Management and Budget (OBM), is conducting a ninety day review of the sUAS NPRM (Colborn, 2015). The OMB has indicated both the FAA and sUAS community lack adequate safety data.
The sUAS which crashed in White House grounds in early February was a contributing factor in the recent push for UAS reform. The current legal restriction on US operated sUAS has enabled foreign companies to gain an advantage in the commercial UAS market:
“Sky-Futures, a British company that dominates the use of drones to collect and analyze inspection data for oil and gas companies, says its business soared 700 percent last year as the normally conservative energy industry embraced the new technology. Co-founder and operations director Chris Blackford said the company is coupling drones with software and a better understanding of what works in the field, giving Sky-Futures ‘a head-start over the U.S because we understand pretty intimately the problems facing the oil and gas market, and how we can solve them with technology.’ Looser regulations outside the U.S. have created pockets of innovation attracting ideas, money and momentum, says Patrick Thevoz, co-founder and CEO of Swiss-based Flyability” – Jeremy Wagstaff, 2015
The international commercial UAS market is valued at $100 billion over the next decade, due to increased UAS applications in the forestry, oil and gas, law enforcement, and agricultural industries. Though military purchases are still dominant, though commercial unmanned aerial vehicle (UAV) spending currently accounts for roughly 12% of the global UAV market and is expected to rise to approximately $82.1 billion between 2015 and 2025 (Ballve, 2014). The FAA has estimated that, if regulations are changed, 7,500 commercial sUAVs could be flying in the US before the end of the decade.
In the global military UAV market, US firms have been losing their market share in recent years to Israeli, European, and Chinese firms due, to strict export controls. To help combat this, the Department of State recently announced it will expedite its review process of foreign military sales with respect to 300 km range 500 kg payload class UAVs—otherwise known as Medium-Altitude Long-Endurance (MALE) UAVs.
General Atomics MQ-9 “Reaper”
Under the 1987 Missile Technology Control Regime (which affects the sale of UAVs), the United States has historically sold few optionally armed UAVs, even among close allies. For example, MQ-9 “Reaper” sales have been limited to the UK, France, Italy, the Netherlands, and recently Spain. With the rise of the Islamic State of Iraq and the Levant, many Gulf allies are requesting additional American arms exports, such as the “Predator” XP. The Department of State has insisted the expedited review process will still adhere to the Missile Technology Control Regime guidelines. Under the foreign military sales program, any potential American UAV customers must:
- Act in accordance of international law, including humanitarian provisions
- Use armed UAVs only under a lawful basis e.g. self defense
- The nation will abstain from using UAVs for domestic surveillance purposes
- UAVs will employ procedures to limit collateral damage
Peter Lichtenbaum and Rachel Stohl argue the new aforementioned restrictions will lead to greater difficulties in exporting American MALE UAVs, despite the Department of State pledge to keep its review process to one year or less. If the US Government continues to inhibit the export of optionally armed American UAVs or similar products, states combating terrorism will find alternate suppliers. For example, the US Government recently barred the sale of additional Cobra helicopter gunships to Nigeria amid human rights concerns; Nigeria subsequently acquired Chinese CH-3 UAVs which it has deployed against Boko Haram militants.
Sources
- Small Unmanned Aerial Systems: What Will the FAA Do? , Mark Colborn , 2015.
http://www.aviationtoday.com/the-checklist/Small-Unmanned-Aerial-Systems-What-Will-the-FAA-Do&thinsp_84243.html - Drone policy improving — but we have a ways to go,
http://m.bizjournals.com/washington/blog/fedbiz_daily/2015/02/drone-policy-improving-but-we-have-a-ways-to-go.html?ana=e_wash_fedbiz&s=newsletter&ed=2015-02-26&u=P7IjntEqPC33GGhyR+ixPA0c3d4c12&t=1424990006&r=full - Game of drones: As U.S. dithers, rivals get a head start, Jeremy Wagstaff, 2015.
http://www.reuters.com/article/2015/03/08/us-tech-drones-idUSKBN0M40VM20150308 - Obama To Sell Armed Drones To More Countries, Patrick Tucker Marcus Weisgerber, 2015.
http://www.defenseone.com/technology/2015/02/obama-sell-armed-drones-more-countries/105495/ - What Obama’s Drone Export Policy Really Means, Peter Lichtenbaum and Rachel Stohl, 2015.
http://breakingdefense.com/2015/02/what-obamas-drone-export-policy-really-means - Obama administration to allow sales of armed drones to allies, Missy Ryan , 2015.
http://www.washingtonpost.com/world/national-security/us-cracks-open-door-to-the-export-of-armed-drones-to-allied-nations/2015/02/17/c5595988-b6b2-11e4-9423-f3d0a1ec335c_story.html - Rep. Hunter to Obama: Send Jordan the Predator XP, Joe Gould , 2015.
http://www.defensenews.com/story/defense/policy-budget/congress/2015/02/05/hunter-to-obama-send-jordan-the-predator-xp/22934783/ - TECH More: Mobile Internet of Things Drones BI Intelligence COMMERCIAL DRONES: Assessing The Potential For A New Drone-Powered Economy, Marcelo Ballve, 2015.
http://www.businessinsider.com/the-market-for-commercial-drones-2014-2
FY 2016 Budget Request Part II – Cyber Security Developments and Budget
The President’s FY 2016 budget includes $14 billion for cyber security funding across all federal agencies, including $5.5 billion for the Department of Defense (DoD). The proposed budget would increase cyber defense spending by ten percent over the enacted FY 2015 budget levels, which is higher than the overall proposed DoD budget increase of seven percent. The increased cyber defense funding within the FY 2016 budget is part of a larger effort by the Federal Government to bolster the nation’s cyber defenses. Other steps taken toward this goal include: the development and integration of new software and systems, increasing the staff of US Cyber Command, Executive Order 13691, and the establishment of the Office of the Director of National Intelligence’s new Cyber Threat Intelligence Integration Center (CTIIC).
The FY 2016 budget request would allocate $582 million towards the integration of the Continuous Diagnostics and Mitigation (CDM) program across federal agencies. CDM stores and catalogues information related to individuals who have network access, and enables network managers to diagnose potential cyber vulnerabilities (Boyd, 2015). Another program to strengthen the cyber defenses of federal agencies is the DHS’s EINSTEIN internet monitoring intrusion prevention program. The increased pace of cyber-attacks has accelerated the deployment of the EINSTEIN Phase 3: the original goal was to implement the program in 2018, but it has now been pushed to a 2015 deployment.
“Einstein 3 is designed to quarantine emails and block malicious Web domains that ‘spoof’ legitimate sites, according to CenturyLink. The service defends the perimeter of federal civilian networks. It senses aberrant activity using threat ‘signatures,’ or tell-tale signs of a hacker derived from U.S. intelligence and private research. These indicators can include certain email headers or IP addresses… DHS ultimately expects to deploy phase 3 across all federal agencies. The new system consists of commercial technologies and government-developed software.” – Sternstein, 2014
The FY 2016 budget request would set aside $587.5 million for DHS cyber operations, including the integration of EINSTEN across federal civilian agencies.
US Cyber Command is has met only half of its staffing requirements for its original goal of maintaining 6,000 personnel by 2016. A total of 780 personnel would be tasked with defending vital industries under the National Mission Teams, 2,700 would be responsible for defending military domain systems, and 1,620 will support combat operations (Sternstein, 2015). Despite its difficulty to fully meet its 6,000 personnel requirement, US Cyber Command has grown rapidly from deploying two cyber mission units to twenty five over the course of 2014. Lt. Gen. Edward Cardon, Commander of US Army Cyber Command, recently indicated the need for more integration between DoD agencies with Cyber Command, as well as for increased collaboration with the private sector (Golden, 2015). Both Executive Order 13691 and CTIIC will foster deeper cooperation between the federal government and the private sector with respect to cyber security issues.
On February 13th 2015, the President issued Executive Order 13691 with the intent of fostering information sharing through Information Sharing and Analysis Organizations (ISAOs) created by the DHS.
“…the development of information sharing organizations that may include industry-specific ISACs but also broaden further to create organizations that may share information in geographical regions or even in response to a particular threat. It also directs the U.S. Department of Homeland Security to work with participants to identify baseline standards and practices to guide information sharing.” – King, 2015
The Office of the Director of National Intelligence’s CTIIC was created with objective of promoting intelligence sharing and coordination between federal agencies on cyber security threats. Under the current system, the DHS, National Security Agency, and US Cyber Command have had somewhat conflicting roles with respect to defending against cyber-attacks (Sanger, 2015). CTIIC will receive a small initial budget of $35 million and is expected to be staffed by roughly 50 personnel from several federal agencies. Overall, the Obama Administration is undertaking a series of robust cyber security measures over the next two years which will significantly mitigate the damage of future cyber-attacks.
Sources
- US Cyber Command Has Just Half the Staff It Needs, Aliya Sternstein , 2015.
http://www.defenseone.com/threats/2015/02/us-cyber-command-has-just-half-staff-it-needs/104847/?oref=d-channelriver - Is Obama’s $14 Billion Cybersecurity Request Enough? , Aliya Sternstein , 2015.
http://www.defenseone.com/technology/2015/02/obamas-14-billion-cybersecurity-request-enough/104421/?oref=d-channelriver - What a New $35 Million Agency Is Expected To Do for US Cyber Defense, Dustin Volz, 2015.
http://www.defenseone.com/technology/2015/02/what-new-35-million-agency-expected-do-us-cyber-defense/105048/?oref=d-channelriver - Obama Administration Plans to Open Center to Fight Cyberattacks, David E. Sanger, 2015.
http://www.nytimes.com/2015/02/11/us/politics/obama-administration-plans-to-open-center-to-fight-cyberattacks.html?partner=rss&emc=rss&_r=2 - Cyber Teamwork Between Federal Agencies Still Too Hard, Says Army Cyber Commander, Hallie Golden, 2015.
http://www.defenseone.com/technology/2015/02/cyber-teamwork-between-federal-agencies-still-too-hard-says-army-cyber-commander/106179/?oref=d-river - Obama asks for $14 billion to step up cybersecurity, Dara Kerr, 2015.
http://www.cnet.com/news/obama-adds-14b-to-budget-for-stepped-up-cybersecurity/ - Obama seeks $14 billion to boost U.S. cybersecurity defenses, Andrea Shalal and Alina Selyukh, 2015.
http://www.reuters.com/article/2015/02/02/us-usa-budget-cybersecurity-idUSKBN0L61WQ20150202 - President budgets $14 billion for cybersecurity, Aaron Boyd, 2015.
http://www.federaltimes.com/story/government/cybersecurity/2015/02/02/president-budgets-14-billion-cybersecurity/22751149/ - FACT SHEET: Cyber Threat Intelligence Integration Center, Office of the Press Secretary, 2015.
http://www.whitehouse.gov/the-press-office/2015/02/25/fact-sheet-cyber-threat-intelligence-integration-center - Continuous Diagnostics and Mitigation (CDM), DHS, 2014.
http://www.dhs.gov/cdm - Obama Signs Info Sharing Executive Order, But Concerns Remain, Rachel King, 2015.
http://blogs.wsj.com/cio/2015/02/13/obama-signs-info-sharing-executive-order-but-concerns-remain/ - Obama to sign executive order on cybersecurity info sharing, Jon Skillings, 2015.
http://www.cnet.com/news/obama-to-sign-executive-order-on-cybersecurity-info-sharing/
FY 2016 Budgetary Analysis – Part I
Earlier in February, the Obama Administration released its fiscal year (FY) 2016 budget request for the Department of Defense (DoD) with a base budget of $534 billion and an overseas operations contingency (OCO) budget of $51 billion. The President’s budget submission does not account for sequestration, which imposes a base budget cap of $499 for the DoD and does not affect the OCO budget. A strong consensus exists among defense and budgetary analysts that Congress is unlikely to repeal the Budget Control Act (BCA) in FY 2016. House Armed Services Committee Representative Adam Smith (D-Wash.) remarked, “I fully expect that Congress will again fight proposals to allow the Department of Defense to deal with the damaging effects of sequestration. We have seen this act before.”
The appropriations and authorization committees will hold hearings on the budget from February to March and are likely to make significant changes to the President’s budget, in a similar manner as the DoD’s FY 2015 budget. Despite the low probability of the base budget exceeding FY 2016 BCA caps, the President’s budget request does provide valuable insight as to the DoD’s current funding priorities, including: prioritization of the Navy and Air Force over the Army, developing technologies and capabilities relevant to great power threats under the third offset strategy, and improving the nation’s cyber security.
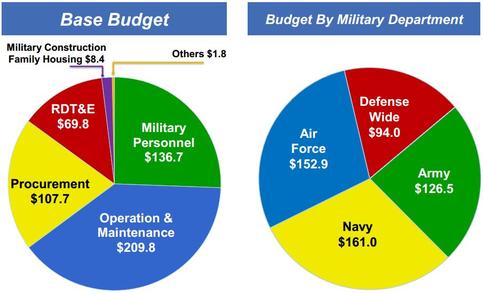
Budget allocations by use and department. Image Credit: DoD.
Under the President’s FY 2016 request, the Air Force and Navy would be the largest beneficiaries of increased spending. The Air Force would receive an additional $16 billion, with a total budget of $152.9 billion, and the Navy would receive an increase of $11.8 billion to bring the total budget up to $161 billion. In contrast, the Army’s budget was increased by only $7 billion, to $126.5 billion. The Air Force received a disproportionally large increase in procurement funding, which comprises more than half of all additional procurement funds (CSIS, 2015). A major production ramp up of Lockheed Martin’s F-35 is expected with an order of 57 aircraft in FYC 2016 from 38 in FY 2015. Air Force officials have consistently stated their desire to protect the F-35 program from the effects of sequestration, along with the Long Range Strike Bomber and Boeing KC-46 tanker programs (Wasserbly, 2014). The prioritization of the Air Force and Navy over the Army is consistent with DoD discussions of the Pacific rebalance which is reliant upon air and sea power. The rebalance was listed first among the five strategic priorities of the FY 2016 budget:
- Rebalance to the Asia-Pacific
- Maintain a strong commitment to security and stability in Europe and the Middle East
- Sustain a global approach to countering violent extremists
- Prioritize and protect key investments in technology
- Reinvigorate efforts to build innovative partnerships
Before his departure, former Secretary of Defense Chuck Hagel had launched a number of defense initiatives designed to promote innovation in technologies relevant to conflicts with great power adversaries like China and Russia. The President’s budget request increased the research development testing and evaluation (RDT&E) budget by $6.3 billion to a total of $69.8 billion. FY 2016 briefing slides listed a few technological areas the DoD hopes to develop as a result, including high energy lasers, rail guns, improve navigation and positioning, and high speed strike. Defense Secretary Ashton Carter is expected to be a vocal advocate of increased DoD investments in RDT&D:
“…the most important advocate for the future will have to be the presumptive Secretary of Defense, Ashton Carter. Protecting these [technology] investments, many of which have their roots in Dr. Carter’s tenure as Deputy Secretary and Under Secretary for Acquisition, Technology and Logistics, will likely be a priority for the new Secretary, and he will be the one to commit to maintaining these future investments over other near-term priorities.” – Center for Strategic and International Studies, 2015
Keep an eye out for Part II of this series, will focus on analysis of cyber developments for FY 2016, including budgetary analysis; the Office of the Director of National Intelligence’s new Cyber Threat Intelligence Integration Center; and Executive Order 13691.
Sources
- Fiscal Year 2016 Budget Request, Office of the Secretary of Defense, 2015.
http://www.defense.gov/pubs/FY16_Budget_Request_Rollout_Final_2-2-15.pdf - DoD Official: No Alternate Sequester Budget in ’16, Paul McLeary, 2016.
http://www.defensenews.com/story/defense/2015/02/19/pentagon-budget-sequestration/23664853/ - DoD Budget Sectors: A Mixed Bag, Paul McLeary, 2016.
http://www.defensenews.com/story/defense/policy-budget/budget/2015/02/11/budget-congress-pentagon-base-supplemental-land-air-naval-cap-bca/23242027/ - Pentagon Unveils $585 Billion Budget Request, Gordon Lubold Marcus Weisgerber, 2015.
http://www.defenseone.com/management/2015/02/pentagon-unveils-585-billion-budget-request/104277/?oref=d-channelriver - Obama Wants More Money for Military Spy Satellites, Lasers, Space Fence, Patrick Tucker, 2015.
http://www.defenseone.com/technology/2015/02/obama-wants-more-money-military-spy-satellites-lasers-space-fence/104364/?oref=d-channelriver - Work: 2016 Budget Submission Reverses Five Year Defense Spending Decline, Sam LaGrone, 2015
http://news.usni.org/2015/01/29/work-2016-budget-submission-reverses-five-year-defense-spending-decline - Navy’s 2016 Budget Preserves Shipbuilding and Aircraft Procurement Plans, Valerie Insinna, 2015.
http://www.nationaldefensemagazine.org/blog/Lists/Posts/Post.aspx?ID=1734 - Obama boosts defense spending, but faces uphill battle, Jon Harper, 2015.
http://www.stripes.com/news/obama-boosts-defense-spending-but-faces-uphill-battle-1.327483 - Pentagon budget 2015: New long-range bomber moves ahead with funding uptick, Daniel Wasserbly, 2014.
http://www.janes.com/article/35244/pentagon-budget-2015-new-long-range-bomber-moves-ahead-with-funding-uptick - The FY 2016 President’s Budget, Ryan Crotty, 2015.
http://csis.org/publication/fy-2016-presidents-budget - The FY 2016 Budget: The Defense Impact, CSIS – Ryan Crotty, Kathleen H. Hicks, Melissa Dalton, John Schaus, Andrew Philip Hunter, Stephanie Sanok Kostro, Maren Leed, Mark W. Lawrence, Thomas Karako, Sharon Squassoni, T.J. Cipoletti, Angela Weaver, 2015.
http://csis.org/publication/fy-2016-budget-defense-impact
RAND Report on Military Caregivers
The RAND Corporation recently published a groundbreaking report, Hidden Heroes America’s Military Caregivers, which depicts the immense scope of military caregiver work in the United States as well as detailing the shortfalls of current veteran’s care policies and programs. The study distinguishes between healthcare providers and military caregivers, with the latter group assisting with activities related to daily living, rather than diagnosing or prescribing treatment. RAND estimates that 5.5 million military care givers support at least 3.8 million disabled veterans nationwide with roughly 20% of military caregivers assisting post-9/11 veterans. This article will provide a summary of the report’s key findings with respect to military caregivers and the efficacy military caregiver related of Government programs.
Through their comprehensive survey, RAND identified several differences between pre-9/11 military caregivers and post-9/11 military caregivers. Individuals caring for service members who joined the military after 9/11 are more likely to be non-white, a friend or spouse of the service member (rather than the service member’s child), employed, are less likely to have a support network, and provide care for an individual who is more likely to have mental health or substance use conditions, when compared to pre 9/11 caregivers. The comparatively higher prevalence of mental health conditions and physical disabilities among post 9/11 veterans has substantially affected the work of post 9/11 military caregivers:
“Two times as many (58 percent) of post-9/11 care recipients have a disability rating compared with pre-9/11 care recipients (30 percent); similarly, two times as many (32 percent) of post-9/11 care recipients have a rating of 70 percent or higher compared with pre-9/11 care recipients (15 percent)… 64 percent of post-9/11 military care recipients have a mental health or substance use disorder; nearly 50 percent of all post- 9/11 military care recipients have depression, twice as many as their civilian and pre-9/11 military counterparts”
The increased burden on post-9/11 caregivers is evident through a host of reported medical ailments including high blood pressure, increased vulnerability to sickness, depression, back pain, and sleep deprivation. The burden of caregiving is especially pronounced in post-9/11 caregivers, largely as a result of limited health care access when compared to pre-9/11 caregivers; roughly 33% of post-9/11 military caregivers do not have adequate healthcare coverage, compared to 20% of pre-9/11 military caregivers.
Despite the stark findings of the report, RAND identified several government programs that have had a demonstrable positive impact on post-9/11 caregivers, including:
- The Special Compensation for Assistance with Activities of Daily Living program provides post-9/11 disabled service members a stipend usable by their primary caregiver, which helps offset the income lost by the military caregiver as a result of higher than average missed work days per month; and
- The Department of Veterans Affair’s Program of Comprehensive Assistance for Family Caregivers provides eligible post 9/11 caregivers with access to healthcare coverage, mental healthcare, a monthly stipend, and caregiver training.
RAND makes a series of recommendations to further improve the quality of care provided by post-9/11 military caregivers and to reduce their burden, including supporting caregiver’s efforts to obtain healthcare coverage, providing training programs that cover an entire spectrum of required skills, and increase public awareness of the vital role of military caregivers.
SO/LIC Symposium Highlights
The National Defense Industrial Association (NDIA) recently hosted its 26th annual Special Operations/Low Intensity Conflict (SO/LIC) Symposium and Exhibition. The three day event hosted several notable speakers including: General Joseph L. Votel – Commander of US Special Operations Command (SOCOM), Lieutenant General Michael T. Flynn (Ret.) – former Director of the Defense Intelligence Agency, and Lieutenant General Marshall B. Webb, Commander – NATO Special Operations Headquarters. The event covered topics such as the challenges related to combating ISIL and a more assertive Russia, as well the increasing demand for Unmanned Aerial Vehicles (UAVs) and the growing desire for commercial off-the-shelf (COTS) technologies.
The threat posed by ISIL was at the centerpiece of many discussions between SO/LIC event speakers and panelists. General Votel stated that at least 19,000 foreign fighters have surged into Iraq and Syria from over 90 countries. Votel further added that SOCOM has been closely observing ISIL’s operations in North Africa. Similarly, Lieutenant General Flynn offered a stark appraisal of the threat posed by ISIL, and cautioned that the ongoing international effort to defeat the group would likely last decades.
Despite the heavy emphasis on combating terrorism at the symposium, the rise in Russian military activity in the Arctic and Eastern Europe was also a frequent discussion topic for General Votel:
“A resurgent Russia is now employing coercive techniques against its neighbor using [special operations] forces, other clandestine capabilities, information operations, other cyber operations and groupings of ethnic proxies and surrogates to drive wedges into our key allies in East Europe…it is important for us to engage and understand what is happening out there and understand the spaces in which they can begin to assert some of their influence.”

RQ-21A Blackjack. Image Credit: US Navy
To combat the wide range of threats to American interests, Votel called for increased Intelligence Surveillance and Reconnaissance (ISR) capabilities from additional UAVs. SOCOM already operates a wide assortment of UAVs, including the RQ-21A Blackjack, RQ-7 Shadow, Viking 400, MQ-1 Predator, and MQ-9 Reaper (Hoffman & Schechter, 2013). Votel indicated that SOCOM would continue to invest in UAV technology, and would work with industry on future projects (Magnuson, 2015). Michael Dumont, Principal Deputy Assistant Secretary of Defense for Special Operations/Low-Intensity Conflict, also stressed SOCOM’s growing interest in incorporating COTS technology as a means to maintain a technologically superior force:
“Many of our adversaries have acquired, developed and even stolen technologies that have put them on somewhat equal footing with the West in a range of areas…Recognizing this future direction requires understanding the current reality: The US government no longer has the leading edge developing its own leading-edge capabilities, particularly in information technology”
Dumont also discussed broader DoD wide measures to ensure the Military’s technological superiority, such as Deputy Secretary of Defense Bob Work’s “Third Offset Strategy” and Under Secretary of Defense for Acquisition, Technology and Logistics Frank Kendall’s “Better Buying Power 3.0”. This new technological offset strategy, in tandem with Better Buying Power 3.0, is meant to secure the technological edge of US forces under a constrained fiscal environment. Both Votel and Dumont also discussed the difficulties of maintaining a high level of operational readiness under sequestration. However, even in the midst of sequestration, SOCOM’s budget has been relatively stable when compared to other portions of the DoD’s budget. Marcus Weisgerber recently examined SOCOM’s FY 2015 budget, which accounted for 1.8% of the DoD’s base and overseas contingency operations (OCO) budget, at $10 billion. The figure does not include the personnel costs of the 70,000 operators under SOCOM or major equipment and weapon procurements which are covered under the budgets of the individual armed services.
Sources
- Peeling the Onion Back on the Pentagon’s Special Operations Budget , Marcus Weisgerber, 2015.
http://www.defenseone.com/management/2015/01/peeling-onion-back-pentagons-special-operations-budget/103905/?oref=d-river - SOCOM’s Gen. Votel Sees Tensions in Arctic, ISIL Expansion as Future Threats, Stew Magnuson, 2015.
http://www.nationaldefensemagazine.org/blog/Lists/Posts/Post.aspx?ID=1722 - Special Ops Commander Discusses Challenges, Priorities, Jim Garamone, 2015.
http://www.defense.gov/news/newsarticle.aspx?id=128047 - Special Operations Eyes Present, Future Threats, Jim Garamone, 2015.
http://www.defense.gov/news/newsarticle.aspx?id=128054 - The text of General Flynn’s speech, Thomas E. Ricks, 2015.
https://foreignpolicy.com/2015/01/27/the-text-of-general-flynns-speech/ - SO/LIC Agenda, NDIA, 2015.
http://www.ndia.org/meetings/5880/Documents/Agenda.pdf - Spec Ops Leaders Want Off-the-Shelf Gear Fast, Paul McLeary, 2015.
http://www.defensenews.com/story/defense/show-daily/solic/2015/01/27/specops-special-operations-technology-jihadists/22425981/ - SOCOM seeks runway-independent UAV, Erik Schechter, 2013.
http://www.flightglobal.com/news/articles/socom-seeks-runway-independent-uav-394362/ - Up to $250M from US SOCOM for L-3’s Viking UAVs, Defense Industry Daily, 2009.
http://www.defenseindustrydaily.com/Up-to-250M-from-SOCOM-for-L-3s-Viking-UAVs-05803/ - SOCOM Wants to Deploy MQ-9 Drones to Remote Areas, Michael Hoffman, 2013.
http://www.military.com/daily-news/2013/09/16/socom-wants-to-deploy-mq9-drones-to-remote-areas.html
State of the Union & Expected Legislative Activity
Of all the measures outlined in the President’s latest state of the union address, the three measures below are the most likely to pass the Republican controlled Congress.
F/A-18F Super Hornets from Strike Fighter Squadron 22 operating from the USS Carl Vinson in support of Operation Inherent Resolve.
Image Credit: U.S. Navy photo by Petty Officer 2nd Class Scott Fenaroli
1. Authorization for the Use of Military Force (AUMF)
During his address, President Obama asked the Congress to pass an AUMF specific to combating ISIL in Iraq and Syria. The President has been in consultation with members of Congress with respect to a new AUMF since late December of 2014, and Speaker of the House John Bohner has indicated a vote will be held on the AUMF by spring of 2015 (Bennett, 2015). A point of contention between Congressional Republicans and Democrats in negotiating an AUMF is the level of discretion the bill will afford to the President, particularly the measures that would prohibit the deployment of ground troops.
The ISIL related AUMF will greatly augment the President’s legal justification for Operation Inherent Resolve, which has been previously justified by the nearly 14 year old AUMF passed after September 11th 2001. Since combat operations in late 2014, the US has launched over 1,800 airstrikes in both Syria and Iraq at a total cost of $1.2 billion.
2. Trans-Pacific Partnership
“…as we speak, China wants to write the rules for the world’s fastest-growing region. That would put our workers and our businesses at a disadvantage. Why would we let that happen? We should write those rules. We should level the playing field” – POTUS
The President made a strong case for the necessity of the ongoing Trans-Pacific Partnership (TPP) free trade agreement over strong objections of congressional Democrats. The TPP is in the final stages of negotiations, and its member states (United States, Canada, Mexico, Peru, Chile, Australia, New Zealand, Japan, Singapore, Vietnam, Brunei, and Malaysia) collectively comprise 40% of the world’s economy. The TPP is considered to a core element of the Pacific re-balance’s economic component and would effectively enable the US to serve as an economic counterweight to China’s growing regional clout (Boyer, 2014).
Several influential Republicans have voiced support for passage of a Trade Promotion Authority (TPA) bill with respect to the TPP. Both Senator Hatch (R-Utah), Chairman of the Senate Finance Committee, and Paul Ryan (R-Wis), Chairman of the House Ways and Means Committee, support passage of the TPA. Evan Medeiros, a senior adviser to the President on the TPP, expects negotiations to be finalized before the end of 2015.
President Obama with Department of Homeland Security (DHS) Secretary Jeh Johnson.
Image retrieved via Politico
3. Cyber Security Bill
In the days leading up to his state of the union address, President Obama rallied support for sweeping new cyber security measures. The President’s proposal would grant legal immunity to companies who share information to the DHS’s National Cybersecurity and Communications Integration Center, and includes measures to protect customer privacy. Company information shared with DHS will be anonymized non-personal data, unlike the information that would have been shared under previously failed Cyber Intelligence Sharing and Protection Act legislation (Tucker, 2015). Furthermore, the data accessed by DHS will primarily relate to computer system information rather than content. The proposal also calls for new laws to criminalize the sharing of stolen US financial data, increases the authority of federal law enforcement to pursue spyware utilized in ID theft, and grants courts authority to close botnets engaged in distributed denial of service attacks (Roberts, 2015).
An ongoing concern with the President’s proposal among scientist and cyber security researchers is that the bill amends the Racketeer Influenced and Corrupt Organizations Act (RICO) laws such that research into system exploits and vulnerabilities will be prosecutable. Research into system vulnerabilities has proven to be among the most effective methods of mitigating vulnerability to cyber attacks (Tucker, 2015).
In the aftermath of the Sony cyber attack, strong bipartisan support exists for improving the nation’s cyber security protections. It remains unclear to the extent in which these new information sharing agreements will improve the private sector and the government’s ability to prevent, contain, and investigate cyber attacks especially from more capable state entities. A recent New York Times article highlighted that despite the NSA’s elaborate and extremely sophisticated methods used to penetrate and monitor North Korean networks, Sony did not receive a warning of an imminent attack. However, the information gleaned from North Korean networks was instrumental towards conniving the President that North Korea was responsible for the attack which subsequently lead to additional sanctions.
Sources
- Obama, GOP Agree the US Needs New War Powers To Fight ISIS, Alex Brown, 2014.
http://www.defenseone.com/politics/2015/01/obama-gop-agree-us-needs-new-war-powers-fight-isis/102861/?oref=d-channelriver - What the Cyber Language in the State of the Union Means to You, Patrick Tucker, 2015.
http://www.defenseone.com/technology/2015/01/what-cyber-language-state-union-means-you/103425/?oref=d-topstory - Hatch says trade promotion authority a necessity, Vicki Needham, 2015.
http://thehill.com/policy/finance/230028-hatch-says-trade-promotion-authority-a-necessity - Obama unveils cybersecurity proposals: ‘Cyber threats are urgent and growing danger’, Dan Roberts, 2015.
http://www.theguardian.com/us-news/2015/jan/13/obama-cybersecurity-bill-privacy-campaigners-warning?CMP=EMCNEWEML6619I2 - Obama, Citing China as Rival, Warns Lawmakers Over Inaction on Trade Measure, Michael Forsythe, 2015.
http://sinosphere.blogs.nytimes.com/2015/01/21/obama-urges-congress-not-to-leave-a-trade-vacuum-for-china/ - State of the Union 2015: Barack Obama urges Congress to approve new use of military force, Philip Ewing and Jeremy Herb, 2015.
http://www.politico.com/story/2015/01/state-of-the-union-2015-barack-obama-isil-114429.html - How Obama Fell Short on Cybersecurity, Joel Brenner, 2015.
http://www.politico.com/magazine/story/2015/01/state-of-the-union-cybersecurity-obama-114411.html?ml=m_u1_1 - Trade tops Ryan’s Ways and Means 2015 agenda, Vicki Needham, 2015.
http://thehill.com/policy/finance/229313-ryan-makes-trade-a-top-priority - Obama urges big labor to accept free-trade deal with Asia, Dave Boyer, 2014.
http://www.washingtontimes.com/news/2014/dec/11/obama-urges-big-labor-accept-free-trade-deal-asia/ - Boehner: Islamic State AUMF Vote by Spring, John T. Bennett, 2015.
http://www.defensenews.com/story/defense/2015/01/21/aumf-islamic-state-isis-boehner/22112617/
DoD Seeks Significant EHR Overhaul
The Department of Defense (DoD) is in the midst of selecting a vendor to overhaul its electronic health record (EHR) systems, which facilitate the transfer of information pertaining to patient’s medical history, conditions, prescriptions, and other data across multiple healthcare providers over time. The Healthcare Management Systems Modernization (DHMSM) program is projected to cost $11 billion through the year 2023. DHMSM will replace the DoD’s existing EHR system, the Armed Forces Health Longitudinal Technology Application (AHLTA), as well as elements of the Theater Medical Information Program-Joint (TIMP-J) and the inpatient Composite Health Care System. When DHMSM launches in 2017, it will become the largest EHR system in the United States, with more than 9.6 million patients associated with over 400 hospitals (Brewin, 2014).
The DoD’s impetus to replace AHLTA stems from the current system’s lack of interoperability with other EHR systems, such as the Veterans Health Information Systems and Technology Architecture (VistA), which is used by the Department of Veterans Affairs (VA). Built-in interoperability in an EHR system is difficult, as only a limited amount of information is easily categorizable or structured; information such as doctor notes or patient descriptions of symptoms is highly variable from patient to patient. Unstructured information makes up approximately 80% of all patient information stored in EHR systems (Konel, 2014).
Despite the significant challenges of designing an interoperable EHR system, four teams of vendors have responded to the DoD’s request:
- Leidos, Accenture Federal, and Cerner
- Computer Sciences Corporation, Hewlett Packard, and Allscripts
- IBM and Epic Systems
- PricewaterhouseCoopers with General Dynamics Information Technology, DSS Inc. and Medsphere
The IBM-Epic bid was the first team to respond, and indicated their interest back in June of 2014. The team has subsequently created an advisory board consisting of reputable EHR experts drawn from the Duke University Health System and School of Medicine, Mercy Health, American Medical Informatics Association, Yale-New Haven Hospital, and Sentara Healthcare (Konkel, 2015). The IBM-Epic team has made significant process in the development of their EHR submission to DHMSM, “IBM and Epic have also built a working and interoperable system at its data center in West Virginia in order to test capabilities and make sure the group of companies had a system that could be deployed quickly if it won the contract. The early version being tested by IBM is already successfully connecting to partner organizations across the country” (Medici, 2015). The Hewlett Packard, Allscripts, and Computer Sciences Corporation will provide a strong source of competition to the IBM-Epic team, as collectively the team has extensive experience with Federal IT projects and EHR systems (McCann & Sullivan, 2014). Relevant experience of other vendors includes Leidos’ (as SAIC) work as one of the major contractors on the TIMP-J program, and Accenture’s efforts to improve Healthcare.gov.
It remains to be seen if DHMSM will meet the DoD’s ambitious objectives, as previous measures to overhaul the DoD’s EHR systems have resulted in few tangible improvements. The DoD had previously sought to integrate its EHR systems with the VA, but the initiative was canceled in 2013 after the program costs were projected to reach nearly $30 billion (Konel, 2014).
Sources
- DoD opens bidding for massive EHR and IT, Erin McCann, & Tom Sullivan, 2014.
http://www.govhealthit.com/news/dod-delivers-rfp-massive-ehr-and-it-modernization - IBM preps for DoD health management modernization contract, Andy Medici, 2015.
http://www.federaltimes.com/story/government/it/health/2015/01/07/ibm-defense-dhmsm-health-contract/21401461/ - Coming Soon: Pentagon’s Multi-Billion Dollar Health Records Contract, Frank Konkel, 2014.
http://www.nextgov.com/defense/2014/04/coming-soon-pentagons-multi-billion-dollar-health-records-contract/83230/ - Possible $11 Billion Contract At Stake for the Pentagon’s Digital Health Records, Frank Konkel, 2015.
http://www.defenseone.com/technology/2015/01/possible-11-billion-contract-stake-pentagons-digital-health-records/102465/?oref=d-river - Race is On for Defense Health Record – but VA Backs Out of Competition, Bob Brewin, 2014.
http://www.nextgov.com/health/health-it/2014/10/race-defense-health-record-va-backs-out-competition/97820/ - Theater Medical Information Program – Joint (TMIP-J), 2013.
http://www.dote.osd.mil/pub/reports/FY2013/pdf/dod/2013tmip.pdf
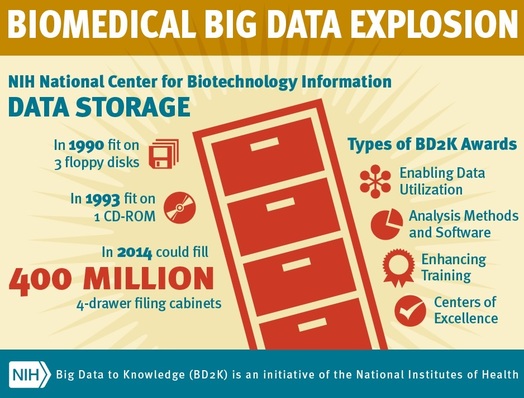
Big Data Developments within NIH
Despite the relatively flat budget in recent years, the National Institutes of Health (NIH) is undergoing changes which will better equip the agency to collect and analyze large biomedical data sets. The cancelation of the NIH’s National Children’s Study (NCS) and the continued investment in the Big Data to Knowledge (BD2K) initiative is indicative of the agency’s efforts to adapt towards recent technological advancements in big data over older more conventional means of collecting biomedical data.
In December of 2014, the NIH announced its decision to terminate the NCS program, which has cost $1.3 billion since 2000. The NCS was envisioned as a means of discovering connections between the environmental factors that appear during an individual’s upbringing and an assortment of medical conditions that could manifest later during adulthood (Tozi & Wayne, 2014), and would have collected data on the development of 100,000 children until they reached the age of 21. However, the NCS program was plagued with a series of problems which led to its termination, including a failure to incorporate new technologies developed over the program’s 14 year period. NIH Director Francis Collins explained, “Science and technology overtook the study’s designers, who weren’t able to incorporate developments such as social media or data collection using mobile devices into their plans.” The NIH’s new Big Data to Knowledge (BD2K) initiative, on the other hand, will seek to capitalize on recent advancements in data analytics and data management.
The BD2K is estimated to cost $656 million through the year 2020, and these funds will go towards developing new tools, software, and procedures to more cost effectively provide biomedical data to researchers. Philip E. Bourne, NIH Associate Director for Data Science, elaborated on the challenges associated with collecting biomedical data, “The future of biomedical research is about assimilating data across biological scales from molecules to population. As such, the health of each one of us is a big data problem. Ensuring that we are getting the most out of the research data that we fund is a high priority for NIH.” NIH hopes that studies which are fully able to capitalize on large data sets will enhance the predictability of medical conditions such as heart attacks and breast cancer, as well as improve current treatment and preventative measures. A total of 12 centers will be established, of which 11 will be responsible for researching broadly applicable aspects of big data science, such as analysis of genomic data, data integration and use, and managing data from electronic health records (NIH, 2014). The last center will be dedicated solely towards coordination between the other 11 BD2K centers.
During FY 2014, NIH spent $32 million on the BD2K initiative, and Stanford University, UCLA, UC Santa Cruz, and USC were the major beneficiaries (Healy, 2014). Over the next four years, the aforementioned universities will receive $38 million towards funding their BD2K projects. USC neuroscientist Paul Thomson described the ongoing problems that result from the current methods of data analytics and data management at the NIH ENIGMA Center for Medicine, Imaging and Genomics project: “’Studies that use such data generate volumes of information that are simply too big to be transferred electronically,’ Thompson said. To review the whole-genome sequencing performed on 815 subjects with Alzheimer’s disease recently, the researchers said they watched delivery trucks disgorge boxes and boxes of disc drives for weeks at a time.”
In summary, NIH is in the process of adapting to advancements in big data which will enable scientists and researchers to assimilate previously incomprehensible volumes of biomedical data; NIH’s commitment towards developing biomedical data analytics and data management is substantial and is likely to have enduring long-term impacts.
Sources
- How the U.S. Government Botched Its Multibillion-Dollar Plan to Beat Childhood Disease, John Tozzi and Alex Wayne, 2014.
http://www.businessweek.com/articles/2014-12-23/how-the-national-childrens-study-fell-apart#p1 - U.S. Child Study Canceled After $1.3 Billion, Alex Wayne, 2014.
http://www.bloomberg.com/news/2014-12-15/huge-u-s-child-health-study-canceled-after-1-3-billion.html - First look: New U.S. spending deal a mixed bag for science, David Malakoff & Jeffrey Mervis, 2014.
http://news.sciencemag.org/funding/2014/12/first-look-new-u-s-spending-deal-mixed-bag-science - Within NIH’s flat 2015 budget, a few favorites, Jocelyn Kaiser, 2014.
http://news.sciencemag.org/funding/2014/12/within-nih-s-flat-2015-budget-few-favorites - US research agencies finally learn their fate, Rebecca Trager, 2014.
http://www.rsc.org/chemistryworld/2014/12/us-america-research-agencies-finally-learn-their-fate-budget - NIH invests almost $32 million to increase utility of biomedical research data, 2014.
http://www.nih.gov/news/health/oct2014/od-09.htm - Big data, meet big money: NIH funds centers to crunch health data, Melissa Healy, 2014.
http://www.latimes.com/science/sciencenow/la-sci-sn-big-data-money-20141009-story.html - About BD2K, NIH, 2014.
http://bd2k.nih.gov/about_bd2k.html#sthash.uHBA8ccw.dpbs