Announcements and news
DJI Phantom-1 sUAS
The Federal Aviation Administration (FAA) is looking to overhaul laws pertaining to the use of small unmanned aerial systems (sUAS), classified as aircraft weighing less than 55 pounds, within the next year. The released Notice of Proposed Rulemaking (NPRM) stipulates measures relating to the operation of non-recreational sUAS in terms of height restrictions, aircraft registration, daytime flight restrictions, operator certification, and line of sight restrictions. The NPRM first step in what is likely to be a yearlong process before enforcement of new regulations begins. The White House Office of Information and Regulatory Affairs, within the Office of Management and Budget (OBM), is conducting a ninety day review of the sUAS NPRM (Colborn, 2015). The OMB has indicated both the FAA and sUAS community lack adequate safety data.
The sUAS which crashed in White House grounds in early February was a contributing factor in the recent push for UAS reform. The current legal restriction on US operated sUAS has enabled foreign companies to gain an advantage in the commercial UAS market:
“Sky-Futures, a British company that dominates the use of drones to collect and analyze inspection data for oil and gas companies, says its business soared 700 percent last year as the normally conservative energy industry embraced the new technology. Co-founder and operations director Chris Blackford said the company is coupling drones with software and a better understanding of what works in the field, giving Sky-Futures ‘a head-start over the U.S because we understand pretty intimately the problems facing the oil and gas market, and how we can solve them with technology.’ Looser regulations outside the U.S. have created pockets of innovation attracting ideas, money and momentum, says Patrick Thevoz, co-founder and CEO of Swiss-based Flyability” - Jeremy Wagstaff, 2015
The international commercial UAS market is valued at $100 billion over the next decade, due to increased UAS applications in the forestry, oil and gas, law enforcement, and agricultural industries. Though military purchases are still dominant, though commercial unmanned aerial vehicle (UAV) spending currently accounts for roughly 12% of the global UAV market and is expected to rise to approximately $82.1 billion between 2015 and 2025 (Ballve, 2014). The FAA has estimated that, if regulations are changed, 7,500 commercial sUAVs could be flying in the US before the end of the decade.
In the global military UAV market, US firms have been losing their market share in recent years to Israeli, European, and Chinese firms due, to strict export controls. To help combat this, the Department of State recently announced it will expedite its review process of foreign military sales with respect to 300 km range 500 kg payload class UAVs—otherwise known as Medium-Altitude Long-Endurance (MALE) UAVs.
General Atomics MQ-9 "Reaper"
Under the 1987 Missile Technology Control Regime (which affects the sale of UAVs), the United States has historically sold few optionally armed UAVs, even among close allies. For example, MQ-9 “Reaper” sales have been limited to the UK, France, Italy, the Netherlands, and recently Spain. With the rise of the Islamic State of Iraq and the Levant, many Gulf allies are requesting additional American arms exports, such as the “Predator” XP. The Department of State has insisted the expedited review process will still adhere to the Missile Technology Control Regime guidelines. Under the foreign military sales program, any potential American UAV customers must:
- Act in accordance of international law, including humanitarian provisions
- Use armed UAVs only under a lawful basis e.g. self defense
- The nation will abstain from using UAVs for domestic surveillance purposes
- UAVs will employ procedures to limit collateral damage
Peter Lichtenbaum and Rachel Stohl argue the new aforementioned restrictions will lead to greater difficulties in exporting American MALE UAVs, despite the Department of State pledge to keep its review process to one year or less. If the US Government continues to inhibit the export of optionally armed American UAVs or similar products, states combating terrorism will find alternate suppliers. For example, the US Government recently barred the sale of additional Cobra helicopter gunships to Nigeria amid human rights concerns; Nigeria subsequently acquired Chinese CH-3 UAVs which it has deployed against Boko Haram militants.
Sources
- Small Unmanned Aerial Systems: What Will the FAA Do? , Mark Colborn , 2015.
http://www.aviationtoday.com/the-checklist/Small-Unmanned-Aerial-Systems-What-Will-the-FAA-Do&thinsp_84243.html - Drone policy improving — but we have a ways to go,
http://m.bizjournals.com/washington/blog/fedbiz_daily/2015/02/drone-policy-improving-but-we-have-a-ways-to-go.html?ana=e_wash_fedbiz&s=newsletter&ed=2015-02-26&u=P7IjntEqPC33GGhyR+ixPA0c3d4c12&t=1424990006&r=full - Game of drones: As U.S. dithers, rivals get a head start, Jeremy Wagstaff, 2015.
http://www.reuters.com/article/2015/03/08/us-tech-drones-idUSKBN0M40VM20150308 - Obama To Sell Armed Drones To More Countries, Patrick Tucker Marcus Weisgerber, 2015.
http://www.defenseone.com/technology/2015/02/obama-sell-armed-drones-more-countries/105495/ - What Obama’s Drone Export Policy Really Means, Peter Lichtenbaum and Rachel Stohl, 2015.
http://breakingdefense.com/2015/02/what-obamas-drone-export-policy-really-means - Obama administration to allow sales of armed drones to allies, Missy Ryan , 2015.
http://www.washingtonpost.com/world/national-security/us-cracks-open-door-to-the-export-of-armed-drones-to-allied-nations/2015/02/17/c5595988-b6b2-11e4-9423-f3d0a1ec335c_story.html - Rep. Hunter to Obama: Send Jordan the Predator XP, Joe Gould , 2015.
http://www.defensenews.com/story/defense/policy-budget/congress/2015/02/05/hunter-to-obama-send-jordan-the-predator-xp/22934783/ - TECH More: Mobile Internet of Things Drones BI Intelligence COMMERCIAL DRONES: Assessing The Potential For A New Drone-Powered Economy, Marcelo Ballve, 2015.
http://www.businessinsider.com/the-market-for-commercial-drones-2014-2
In early March, Congress passed a $39.7 billion budget for the Department of Homeland Security (DHS) which is $400 million dollars greater than the enacted FY 2014 levels. Most components of DHS received a funding increase, but the FY 2015 budget prioritizes a series of initiatives to strengthen border security through hiring new personnel, developing new biometric identification technologies, and supporting previous efforts to improve border infrastructure. Part II of this series on the FY 2015 DHS budget will detail significant increases in the capability of the Coast Guard as a result of the FY 2015 budget, as well as trends within the agency.
CBP MQ-9 "Reaper" UAV
Immigration Customs and Enforcement (ICE) received a disproportionately large increase in funding relative to other DHS components at $944 million, a 13% increase, which is 16% greater than the figure originally requested by the Obama Administration. ICE will spend $62 million this year to hire new support staff and agents to counter human trafficking and drug smuggling operations (Katz, 2015). US Customs and Border Protection (CBP) received a roughly 1% increase in funding, but is also expected to make significant increases to its personnel. The FY 2015 budget funds 23,775 CBP officers and 21,370 border patrol agents. CBP is also expanding its investment into its biometric identification system called IDENT.
IDENT currently contains the finger prints and facial images of more than 170 million foreigners, as well as 600,000 iris templates (Sternstein, 2015). Planned upgrades to IDENT will enable CBP to match more than 10 million iris and facial images through an expansion of IDENT infrastructure. While the IDENT upgrades are expected to improve the system’s identification capabilities, the system is expected to have difficulty in compensating for changes to the iris over time,
“Iris matching is by no means 100 percent accurate. The texture of an individual's iris changes with aging -- though by how much is controversial, and engineers have demonstrated that ID thieves can hack iris template databases to duplicate other people's eye patterns. ‘We’re trying to get enough knowledge right now on how to do iris [scans] to be able to actually process the images we’ve been collecting for a couple of years now,’ Fritzsche [director of identify technology at DHS Office of Biometric Identity Management] said during public remarks. ‘That’s what we’re doing with this pilot.’” - Aliya Sternstein, 2015
The FY 2015 DHS budget also funds a biometric exit mobile application under CBP as well as 95,000 flight hours of border surveillance; CBP operates a small fleet of MQ-9 unmanned aerial vehicles (Katz, 2015).
In conjunction with the Canadian Border Service Agency, the Department of Transportation, and Transport Canada, CBP completed a series of border infrastructure projects under the Border Infrastructure Investment Plan (BIIP) I and II, which were completed in 2014. BIIP 1.0 upgraded the infrastructure in seven key Canada-US border sites, and BIIP 2.0 expanded the program to include the top 20 crossings by two-way trade, 25 major ports and the top 15 crossings based on two-way non-commercial traffic volume (Transport Canada, 2014). BIIP 2.0 includes investments in intelligent transportation systems such as wait time measurement technology, advanced traveler information systems, and traffic management centers. Cumulatively, BIIP 1.0 and 2.0 will improve security, reduce wait times, and improve the reliability of shipments.
In summary, DHS is in the process of making significant additions to border security through new technologies, upgraded border infrastructure, and additional personnel. However, boosting border security does not come without a cost: the Transportation Security Administration will face a $94.3 million reduction in its budget, as well as a cap on airport screening personnel (Medici, 2015). Furthermore, DHS’ FY 2015 budget request reduced funding for the Science and Technology directorate by nearly 10% when compared to the enacted FY 2014 budget. The prioritization of border security and the development of biometric identification technologies reflects shifting agency priorities. Cyber security is also receiving increased attention within DHS as shown by the creation of the new National Cybersecurity and Communications Integration Center and developments within the Coast Guard which will be discussed in Part II.
Sources
- Budget in Brief FY 2015, Department of Homeland Security, 2015.
http://www.dhs.gov/sites/default/files/publications/FY15BIB.pdf - Shutdown averted: Congress funds DHS through 2015, Andy Medici, 2015.
http://www.federaltimes.com/story/government/dhs/management/2015/03/03/dhs-shutdown/24323381/ - Homeland Security To Roll Out Biometrics Along the Border This Summer, -Aliya Sternstein, 2015
http://www.defenseone.com/technology/2015/01/homeland-security-roll-out-biometrics-along-border-summer/103968/?oref=search_DHS - Boats, Biometrics and Other Items in the Homeland Security Funding Bill, Eric Katz, 2015.
http://www.defenseone.com/politics/2015/03/boats-biometrics-and-other-items-homeland-security-funding-bill/106806/?oref=search_DHS - Congress narrowly averts DHS shutdown, Andy Medici, 2015.
http://www.federaltimes.com/story/government/dhs/management/2015/02/27/dhs-shutdown/24158055/ - Border Infrastructure Investment Plan Canada – United States December 2014
- Borders, Transport Canada, 2015.
http://www.tc.gc.ca/eng/policy/acg-acgd-menu-borders-2144.htm

National security cutter Bertholf, EADS HC-144, and H-65 helicopter
The US Coast Guard (USCG) received $10 billion for fiscal year (FY) 2015, $435.9 million above the Obama Administration’s FY 2015 budget request. The FY 2015 budget, in conjunction with the newly released Navy maritime strategy, A Cooperative Strategy for 21st Century Seapower, provides insight towards future USCG priorities, procurement programs, and sought after capabilities and technologies.
The new maritime strategy outlined broad Navy priorities since the release of the earlier 2007 edition. At the Department of the Navy level, the new maritime strategy indicates that the service will place a greater emphasis on all domain access, the ability to operate in contested environments on the surface, undersea, space, cyber, electromagnetic spectrum, etc. The Navy’s decision to prioritize all domain access, so that it is nearly equivalent to the Navy’s nuclear deterrence mission, is a response to anti-access area denial threats from China and Russia (Freedberg, 2015). The document also emphasizes the role of electronic warfare, cyber warfare, working with US allies, and increasing the Navy’s forward presence in the Indo-Asia-Pacific and the Middle East.
At the USCG level, the document indicated the Coast Guard would prioritize the development of the service’s cyber defense capabilities, and allocate additional resources towards the Western Hemisphere as well as the Arctic and the Antarctic. The USCG will release its first cyber security strategy next month, which will underscore the importance of protecting the nation’s heavily automated ports, establish situational awareness to cyber events, and protect USCG assets (Watkins, 2015). Rear Admiral Peter Brown, Assistant Commandant for Response Policy recently underscored the need for the USCG to embrace its new cyber security role:
“So many aspects of maritime transportation are now reliant on computer controls -- not only the more traditional navigation and communications technology but also the physical responses of facilities and vessels such as unmanned systems that unload and scan cargo containers…We have to make sure from a Coast Guard perspective that the supply chain is secure from a cyber-perspective. The Coast Guard needs to be aware of what threats and challenges are out there to the global maritime transportation system through cyber access”
In terms of geographic priorities, commandant Zukunft explained the shift of resources to the Western Hemisphere is in response to the rising level of violence in Central and South America (Grady, 2015). Zukunft explained the influx of unaccompanied children from Latin America to the US border in the summer of 2014, in addition to the ongoing demand for counter narcotic missions, had an impact on the service’s decision to base more resources in the Western Hemisphere. Zukunft justified the increased resources dedicated to both the Arctic and Antarctic as a result of rising international maritime activity in both areas. The Artic in particular is likely to receive more resources as a result of significantly increased Russian activity in the region, following the seizure of Crimea and the ongoing territorial disputes between Russia, Canada, and Denmark. In order to facilitate the increased demand for the USCG in both the Western Hemisphere and the Artic, the FY 2015 budget provides billions for new systems and platforms.
ScanEagle unmanned aerial system (UAS) launching from the USCG cutter Bertholf
The FY 2015 budget would also fund the purchase of additional frigate-sized national security cutters, HC-130J maritime surveillance and transport aircraft, H-60 helicopters, and continue the development of both the polar icebreaker and icebreaker tugs. The USCG is also experimenting in deploying UAS from its fleet of cutters and icebreakers. The Boeing Insitu ScanEagle shown above is expected to be procured in the Coast Guard’s FY 2016 budget, with deployments beginning in FY 2017 following successful ship based tests and sea trials (Rico, 2013). The USCG also tested the AeroVironment RQ-20 Puma in August 2014; the RQ-20 flew from the USCGC Healy icebreaker operating in the Arctic (Smith, 2014). The deployment of UAS from both cutters and icebreakers would greatly enhance the USCG’s maritime surveillance and intelligence surveillance and reconnaissance capabilities.
The USCG is in the midst of a transformational process to prioritize the Western Hemisphere, the Arctic, and significantly augment its cyber defense capabilities. Procurement priorities over the next few years will focus on the modernization of its fleet of national security cutters, gaining extended maritime surveillance capabilities via UAS, and developing new icebreakers to maintain the United States’ presence in the Arctic. However, the continuation of sequestration into FY 2016 will constrain the USCG’s ability to field a more modern fleet of cutters, as well as other comparatively expensive platforms such as icebreakers.
Sources
- Coast Guard cyber plan to focus on ports, shipping, Steve Watkins, 2015.
http://www.federaltimes.com/story/government/cybersecurity/2015/03/12/coast-guard-cyber-plan-ports-shipping/70203712/ - Committee Releases Fiscal Year 2015 Homeland Security Appropriations Bill, 2015.
http://appropriations.house.gov/news/documentsingle.aspx?DocumentID=393930 - Winning The War Of Electrons: Inside The New Maritime Strategy, Sydney J. Freedberg, Jr., 2015.
http://breakingdefense.com/2015/03/winning-the-war-of-electrons-inside-the-new-maritime-strategy/ - Boats, Biometrics and Other Items in the Homeland Security Funding Bill, Eric Katz, 2015.
http://www.defenseone.com/politics/2015/03/boats-biometrics-and-other-items-homeland-security-funding-bill/106806/?oref=search_DHS - House OKs Controversial DHS Funding Measure, John T. Bennett, 2015.
http://www.defensenews.com/story/defense/policy-budget/congress/2015/01/14/homeland-security-dhs-immigration-house/21752693/ - UAV a success for Coast Guard in major drug bust, Antonieta Rico, 2013.
http://www.militarytimes.com/article/20130810/NEWS03/308100005/UAV-success-Coast-Guard-major-drug-bust - Coast Guard Icebreaker Launches, Lands First Arctic Drone, Matthew F. Smith, 2014.
http://www.knom.org/wp/blog/2014/08/31/coast-guard-icebreaker-launches-lands-first-arctic-drone/ - Maritime Security: Sneak Preview of the Coast Guard’s Cybersecurity Strategy, Lt. Jodie Knox, 2015.
http://inhomelandsecurity.com/maritime-security-sneak-preview-of-the-coast-guards-cybersecurity-strategy/ - Coast Guard Information Technology, Sensor Needs Go Unfilled, Stew Magnuson, 2014.
http://www.nationaldefensemagazine.org/archive/2014/December/Pages/CoastGuardInformationTechnologySensorNeedsGoUnfilled.aspx - Coast Guard Closer to Acquiring Ship-Based Drones, Stew Magnuson, 2014.
http://www.nationaldefensemagazine.org/archive/2014/July/Pages/CoastGuardClosertoAcquiringShip-BasedDrones.aspx - Cyber and Electronic Warfare Stand Out in Navys Maritime Strategy, Kris Osborn, 2015.
http://www.military.com/daily-news/2015/03/13/cyber-and-electronic-warfare-stand-out-in-navys-maritime.html
The inability of the Pentagon to rapidly assimilate new technologies and cut bureaucratic red tape is increasingly being perceived as not merely a poor use of tax dollars, but as a strategic liability by both senior DoD officials and members of Congress (Freedburg, 2015). In a March address to the Center for Strategic and International Studies, Senate Armed Services Committee (SASC) Chairman John McCain compared the 18 month standard innovation cycle in the private sector to the Pentagon acquisition cycle, which can last for up to 18 years. McCain argued that the glacial pace of Pentagon acquisitions threatens to undermine the nation’s technological superiority, and the inefficient allocation of taxpayer dollars during sequestration further exacerbates the acquisition processes negative impact on national defense.
In an effort to address these concerns, Under Secretary of Defense for Acquisition, Technology and Logistics Frank Kendall ordered the implementation of the DoD’s new acquisition reform effort, “Better Buying Power (BBP) 3.0.” The BBP 3.0 memo, released Thursday, offers a series of initiatives to improve the efficiency of future acquisition programs, with the intent of cultivating the long-term technological superiority of the US military in the face of increasingly advanced systems fielded by both Russia and China. The BBP memo concentrates on 34 areas of focus, such as increasing the use of prototyping and experimentation, emphasizing technology insertion, modular system design and open system architectures, the ability to strengthen cybersecurity throughout a product’s lifecycle, increased access to small business research and development, etc. Many of the new measures are aimed at incentivizing nontraditional defense contractors, such as Silicon Valley technology companies, to engage with the Pentagon, and at increased collaboration with allied nations (Mehta, 2015).
Undersecretary Frank Kendall described the design of the long range strike bomber (LSRB) as an example of BBP 3.0 recommendations including planned technology insertion that would enable competitions for bomber upgrade and sustainment contracts
Overall, the document underscores the DoD’s renewed vigor to rapidly assimilate new technologies and manage excessive bureaucracy. BBP 3.0 will likely be accompanied by new legislation being drafted by House Armed Services Committee Chairman Mac Thornberry in consultation with SASC Chairman John McCain. Thornberry’s legislation will take an incremental realist approach to acquisition reform, which starts by mitigating the unintended consequences of past reform efforts such as the Weapons Systems Acquisition Reform Act of 2009 (Freedburg, 2015). Thornberry’s bill would also consolidate program requirements and reduce redundant reporting standards:
“Many reports and requirements that are currently handled as separate, time-consuming processes would be consolidated into a single strategy document. Other reports and requirements would simply go away. ‘Probably one of the biggest things,’ the staffer said, is downgrading many ‘certifications’ to mere ‘determinations’: That’s not just a change in terminology. It marks a major reduction in the amount of time and lawyers involved. Milestone A decisions to start developing technologies no longer require any certifications at all, only determinations. Milestone B decisions to start actual engineering and manufacturing development (EMD) would still require certifications, but not as many.” - Sydney J. Freedberg, Jr., 2015
DoD officials have been largely receptive of Thornberry’s proposals, including Undersecretary Kendall. In summary, the combination of BBP 3.0 and new acquisition reform legislation has the potential to mitigate the damage of prior acquisition reform efforts and improve the efficacy of new programs. BBP 3.0 will enable the DoD to make the required investments in its third offset strategy such as robotics, big data, miniaturization, autonomous systems, etc.
Sources
- Work: Better Buying Power 3.0 Strives to Enhance U.S. Tech Edge, Jim Garamone, 2015
http://www.defense.gov/news/newsarticle.aspx?id=128558 - Pentagon Begins Better Buying Power 3.0, Aaron Mehta, 2015
http://www.defensenews.com/story/defense/policy-budget/budget/2015/04/09/better-buying-power-3-launches/25519245/ - Pentagon spotlights cyber in Better Buying Power 3.0, Amber Corrin, 2015
http://www.c4isrnet.com/story/military/tech/2015/04/09/pentagon-spotlights-cyber-in-better-buying-power-30/25538627/ - Frank Kendall: Better Buying Power 3.0 Implementation Guide in The Works, Ross Wilkers, 2015
http://www.executivegov.com/2015/03/frank-kendall-better-buying-power-3-0-implementation-guide-in-the-works/ - Cut Red Tape: HASC Chair Thornberry Rolls Out 1st Major Acquisition Changes , Sydney J. Freedberg, Jr., 2015
http://breakingdefense.com/2015/03/thornberry-to-roll-out-increment-one-of-acquisition-reform/ - The Imperative of Defense Reform: Serious Challenges for a Serious SecDef. , John G. McGinn, Stephen Rodriguez and Peter Lichtenbaum, 2015
http://warontherocks.com/2015/02/the-imperative-of-defense-reform-serious-challenges-for-a-serious-secdef/ - Kill Old Procurement Laws, Congress! Stackley, Punaro, Sydney J. Freedberg, Jr., 2015
http://breakingdefense.com/2015/01/kill-old-procurement-laws-congress-stackley-punaro/
The National Institutes of Health Information Technology Acquisition and Assessment Center (NITAAC) recently awarded its Chief Information Officer–Commodity Solutions (CIO-CS) Government-wide Acquisition Contract (GWAC), valued at $20 billion, to 65 companies. CIO-CS is an indefinite-delivery/indefinite-quantity information technology (IT) contract with a duration of ten years (Boyd, 2015). While the contract is primarily a health IT vehicle, it will also include a host of other services such as deployment and installation, engineering studies, web and video-conferencing, big data, virtualization and health and biomedical IT, maintenance and training, enterprise licenses and extended warranties, and cyber security (NIH, 2015). The NIH incorporated numerous changes into the CIO-CS as a result of the previous Electronic Commodities Store (ECS) III GWAC.
In contrast to the ECS III, the CIO-CS and will place a premium on the adaptability of companies providing IT services:
“With CIO-CS we saw an evolving, enormous change in the IT marketplace when it comes to commoditized services and managed services and cloud services…We wanted to build a contract that had contract holders that were going to be able to meet those needs as they change. They are changing very, very quickly to be able to not only provide the straight laptops, desktops and hardware equipment; but to be able to buy those more sophisticated software licenses, being able to get the cloud services that they need. They will continue to evolve with mobility and infrastructure services that agencies are looking at…Contract holders really had to prove that they are going to be able to be relevant and meet those ever-changing needs that the government has over the next 10 years.” – NITAAC Program Director Robert Coen
The CIO-CS contract awardees include a wide range of firms including multibillion dollar companies such as AT&T and Hewlett Packard, as well as 44 small businesses of varying types:
- 6 service-disabled veteran-owned small business
- 8 HUBZone
- 14 women-owned
- 6 8(a), seven economically disadvantaged women-owned small business
A full listing of CIO-CS contract holders available at the NITAAC website. The number of small business participating in CIO-CS is consistent with prior NIHAAC commitments to award fifty percent of the total $8 billion awarded in previous GWACS over the past two and a half years (Coen, 2015).
In summary, NITAAC requirements reflect the growing interest within the NIH to modernize its IT services, transition towards a more cloud-based infrastructure, and address cyber security issues. Growing concerns over inadequate cyber security measures are likely to profoundly affect federal health IT contractors in the coming years. For example, the National Institute of Standards and Technology (NIST) released draft requirements relating to the management of controlled unclassified sensitive information; the new NIST requirements will supplement existing Federal Information Security Management Act (Ravindranath, 2015).
Suggested Reading
Sources
- NIH awards new government-wide IT contract, NIH, 2015.
http://www.nih.gov/news/health/apr2015/nitaac-17.htm - Chief Information Officer – Commodities and Solutions (CIO-CS), FBO, 2015.
https://www.fbo.gov/index?s=opportunity&mode=form&id=c225c2cac56ee3a5ac1a34b922c844dc&tab=core&_cview=1 - Coen dissects the CIO-CS GWAC, Aaron Boyd, 2015.
http://www.federaltimes.com/story/government/interview/program-view/2015/04/14/coen-dissects-cio-cs-gwac-coming-soon/25773019/ - NIH launches competition for $20B CIO-CS program, Steve Watkins, 2014.
http://archive.federaltimes.com/article/20140508/ACQ03/305080006/NIH-launches-competition-20B-CIO-CS-program - Robert Coen: NIH Seeks To Adapt It Needs In ‘Evolving’ Marketplace Through New GWAC, Anna Forrester, 2015.
http://www.executivegov.com/2015/04/robert-coen-nih-seeks-to-adapt-it-needs-in-evolving-marketplace-through-new-gwac/ - NIH awards $20B CIO-CS acquisition contract for IT, Michael O'Connell, 2015.
http://www.federalnewsradio.com/459/3838919/NIH-awards-20B-CIO-CS-acquisition-contract-for-IT - Contractors Could Get New Rules For Handling Sensitive Government Data, Mohana Ravindranath, 2015
http://www.nextgov.com/big-data/2015/04/nist-refining-rules-non-federal-groups-handling-federal-data/109399/ - NIH Awards New Government-Wide IT Contract, Covers Cybersecurity, Big Data Solutions, Homeland Security Today Staff, 2015
http://www.hstoday.us/briefings/news-shorts/single-article/nih-awards-new-government-wide-it-contract-covers-cybersecurity-big-data-solutions/c1579750346dd8aef8eed11db1b22d81.html
Fort Meade MD, place of performance for the contract
In late April, the Defense Information Technology Contracting Organization released a request for proposals (RFP) concerning US Cyber Command’s (USCYBERCOM) $475 million indefinite delivery, indefinite quantity omnibus contract.* The RFP outlines 20 services selected contractors will provide:
- Knowledge Management
- Records Management
- Cyber Operations
- Planning; Science and Technology/Research and Development
- Cyber Focused Training
- Cyber Exercise
- Engagements
- Logistics
- Integrated Technology Support
- CybersecurityProject Analysis
- Program Management
- All-source Intelligence
- Business Process ReengineeringSecurity
- Strategy and Policy and Doctrine Development
- Administrative Support
USCYBERCOM is outsourcing work to the private sector, including sensitive cyber operations and offensive roles, in an effort to meet high operational demand (Sternstein, 2015). Under the new cybersecurity strategy, the Department of Defense will field 133 cyber mission force teams by 2018, including: 13 national mission teams, 68 cyber protection teams, 27 combat mission teams, and 25 support teams. However, USCYBERCOM has only met half of its staffing requirements for its original goal of maintaining 6,000 personnel by 2016. USCYBERCOM’s difficultly in acquiring skilled cybersecurity employees is largely a result of intense competition with the private sector.
Similarly, the NSA has been under significant pressure to sustain its workforce despite Congressional exemptions in hiring authority regulations combined with comparatively high wages relative to other federal agencies. NSA human resources director John Yelnosky noted:
“We’re throwing the kitchen sink at them from our standpoint…And they’re writing in to us, as they leave NSA, in their exit interviews, ‘I’m leaving to double my salary…The competition out there is really fierce and particularly for these folks that we make a big investment in, and we feel those losses very keenly”
As the economy continues to improve, competition between the private sector and federal agencies is likely to both accelerate and favor the private sector; the private sector’s greater degree of flexibility in managing its workforce in terms of wages, perks, providing greater opportunity for career advancement, etc. in conjunction with its ability to more quickly assimilate of new technologies grants it a decisive advantage over the public sector. Substantial cybersecurity contracts similar to the USCYCBERCOM omnibus will continue as federal agencies will be unable to meet demand for cybersecurity capabilities. For example, $100 million cyber expertise contract designed to attract subject matter experts in intelligence, national security, counterterrorism, and technology (Konkel, 2015). *CYBERCOM recently cancelled this contract, and is expected to relaunch the opportunity by October 1st. Competition for cyber security personnel will most likely continue, regardless of when the opportunity is released.
Related Reading
Sources
- CYBERCOM To Outsource $475 Million of Work To Stand Up Command, Aliya Sternstein, 2015.
http://www.defenseone.com/technology/2015/05/cybercom-outsource-475-million-work-stand-command/111718/?oref=d-river - DOD’s new Internet strategy boosts role in defending “US interests”, 2015.
http://arstechnica.com/information-technology/2015/04/the-x-men-dod-embraces-silicon-valley-ethos-with-new-innovation-unit/ - United States Cyber Command (USCYBERCOM) Omnibus Contract, FBO, 2015.
https://www.fbo.gov/index?s=opportunity&mode=form&id=081a3d229dcf843bd8bb0d77c42ef465&tab=core&tabmode=list&= - The Department of Defense Cyber Strategy, DoD, 2015.
http://www.defense.gov/home/features/2015/0415_cyber-strategy/ - The NSA’s Fight To Keep Its Best Hackers, Jack Moore, 2015.
http://www.defenseone.com/management/2015/04/nsas-fight-keep-its-best-hackers/110401/ - US Cyber Command Has Just Half the Staff It Needs, Aliya Sternstein, 2015.
http://www.defenseone.com/threats/2015/02/us-cyber-command-has-just-half-staff-it-needs/104847/?oref=d-channelriver
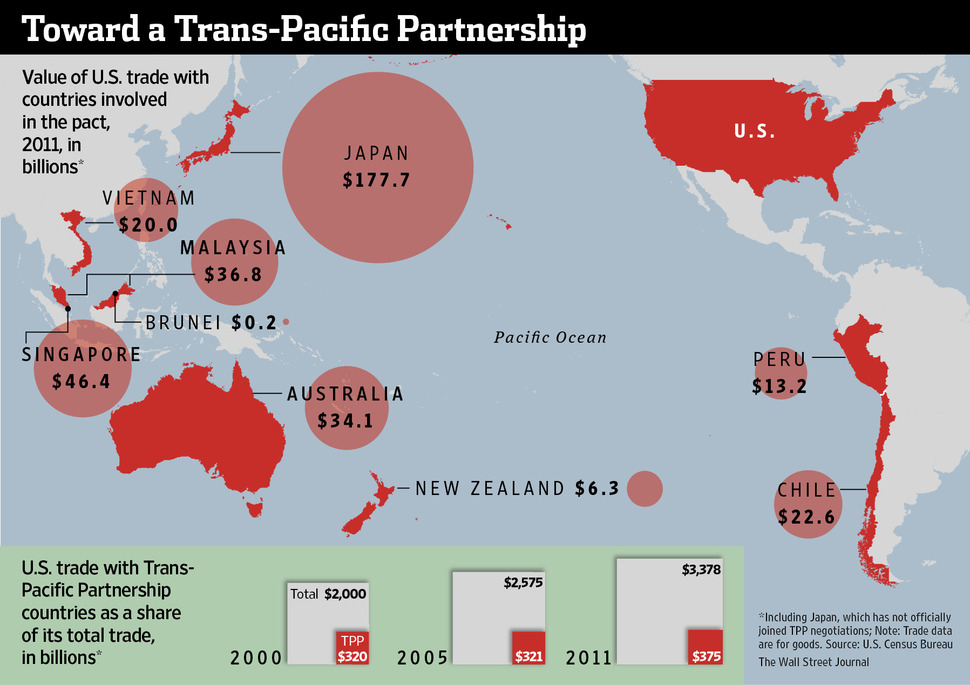
US trade with TPP negotiating partners. Image Credit: The Wall Street Journal
The United States Senate passed a bill over Memorial Day weekend which would grant the President Trade Promotion Authority (TPA) with respect to the Trans-Pacific Partnership (TPP) free trade agreement. The TPA, or “fast track” authority, is critical to securing a final TPP free trade agreement with eleven other countries, as it effectively grants the President authority to negotiate on behalf of the United States. Furthermore, the TPA would limit Congress to a simple up or down vote on the final TPP terms, without the ability to subsequently add amendments pending the conclusion negotiations. The 62-37 vote in favor of the TPA overcame the objections of labor groups and progressives who have railed against the perceived lack of labor protections, secrecy of negotiations, and stringent intellectual property regulations. The House will take up the TPA after returning on June 1st, where it will face numerous hurdles from pro-labor democrats, “poison pill” amendments such as the proposed currency manipulation measure – which the President indicated he would veto, and conservatives, who are hesitant to grant the President negotiating authority on behalf of the United States.
The TPP will eliminate tariffs across 11,000 categories among the twelve nations in the agreement, and will affect $882 billion in US import and $727 billion in US export flows (Ferguson, McMinimy, and Williams, 2015). While estimates on US growth as a result of the TPP vary, a consensus exists that the induced US growth would be a minimal net positive within the range of 0.13-0.19% GDP, or less than a $40 billion net increase in social welfare. The calculations of net benefits accrued as a result of the TPP factor the relative increases in US economic sectors as a result of losses in other areas of the economy, e.g. US agricultural exports are expected to rise as a result of the TPP, in contrast to a decline in manufacturing. Overall, the changes will be minimal, as the United States economy is comparatively open relative to other TPP partners such as Japan and Vietnam, and US firms already compete with low wage manufacturing centric economies:
“For those who worry that, after the TPP, the United States would have to compete against low-wage countries — it’s too late. As Zachary Karabell notes, we are already living in a free-trade world. The average tariff in the developed world is about 3 percent. And in the past three decades, developing countries have cut their tariffs substantially as well. The World Trade Organization notes that China’s average is less than 10 percent today, down from about 40 percent in 1985.” – Fareed Zakaria, 2015
The primary US motivation for passing the TPP given the minimal gains to domestic economic growth is geopolitics. The TPP is cornerstone of the Obama Administration’s economic aspect of the Asian rebalance, which seeks to assert and preserve US influence in the Pacific as a hedge to China’s increasing military and economic influence. The greatest beneficiaries of the TPP are countries whom both the United States and China are vying for influence rather than traditional stalwart US allies such as Japan and Australia. Vietnam and Malaysia are expected to benefit disproportionately from the TPP with 28% and 6% additional GDP growth, respectively, by 2025 (Petri, Plummer and Zhai, 2013). Proponents of the TPP, such as former Undersecretary of Defense for Policy Michèle Flournoy, argue the TPP is a means to demonstrate long-term US commitment to Asia and prevent China from creating trade policies in the region contrary to US interests. Secretary of Defense Aston Carter made similar remarks and stressed, “Passing TPP is as important to me as another aircraft carrier”.
The Obama Administration has been hard-pressed to continue with the economic and diplomatic aspects of the re-balance given the series of crises in the Middle East and Ukraine, but the Military aspect of the re-balance is well underway. The Navy will base 60% of all its ships in the Pacific by 2020 including additional forward deployed ships and both the Navy and the Air Force will prioritize their most modern equipment to PACOM including all DDG-1000 destroyers and the first F-35s to be deployed overseas.
Sources
- Senate advances fast-track trade bill sought by Obama, Richard Cowan, 2015.
http://www.reuters.com/article/2015/05/21/us-usa-trade-idUSKBN0O61WJ20150521 - The Trans-Pacific Partnership (TPP) Negotiations and Issues for Congress, Ian F. Fergusson, Mark A. McMinimy, and Brock R. Williams, 2015.
https://www.fas.org/sgp/crs/row/R42694.pdf - Trans-Pacific Partnership: Geopolitics, Not Growth, Samuel Rines, 2014.
http://nationalinterest.org/commentary/trans-pacific-partnership-geopolitics-not-growth-10157 - A Trade Deal With a Bonus For National Security, Michèle Flournoy and Ely Ratner, 2015.
http://www.wsj.com/articles/michele-flournoy-and-ely-ratner-a-trade-deal-with-a-bonus-for-national-security-1425854510 - Protecting the Future of Trade in Asia, Cathy Holcombe, 2015.
http://www.wsj.com/articles/protecting-the-future-of-trade-in-asia-1432140387?KEYWORDS=TPP - White House Threatens to Veto Trade Bill Over Currency Measure, William Mauldin, 2015.
http://www.wsj.com/articles/white-house-threatens-to-veto-trade-bill-over-currency-measure-1432068819?KEYWORDS=TPP - You can’t stop the trade machine, Fareed Zakaria, 2015.
http://www.washingtonpost.com/opinions/you-cant-stop-the-trade-machine/2015/05/14/208d74a2-fa6e-11e4-a13c-193b1241d51a_story.html - On TPP, it looks like 1993 all over again, Raoul Lowery Contreras, 2015.
http://thehill.com/blogs/pundits-blog/finance/242347-on-tpp-it-looks-like-1993-all-over-again
http://thehill.com/blogs/floor-action/senate/242583-reid-obama-loves-the-export-import-bank - Reid: Obama 'loves' the Export-Import bank, Jordain Carney, 2015.
http://thehill.com/policy/finance/overnights/242734-overnight-finance-moderate-dems-deal-blow-to-shelbys-bill
Draganflyer X6 small unmanned aerial system (sUAS)
The Department of Justice (DOJ) recently announced a series of guidelines for the use of unmanned aerial system by domestic law enforcement and federal agencies. While the DOJ report is fully cognizant of the significant potential for UAS within law enforcement, the document states that all UAS use must conform to existing privacy and civil liberty protections:
“UAS must be operated consistent with the U.S. Constitution. The Fourth Amendment protects individuals from unreasonable searches and seizures and generally requires law enforcement to seek a warrant in circumstances in which a person has a reasonable expectation of privacy. Moreover, Department personnel may never use UAS solely for the purpose of monitoring activities protected by the First Amendment or the lawful exercise of other rights secured by the Constitution and laws of the United States.” – DOJ, 2015
The restrictions outlined by the DOJ largely apply to existing manned surveillance platforms. In an effort to improve accountability and transparency, the Deputy Attorney General will review DOJ UAS issues on an annual basis and will require federal agencies to keep logs of every flight (Moon, 2015). Furthermore, all data retrieved by UAS is subject to existing data storage and protection laws.
The release of DOJ guidelines on the use of UAS by law enforcement indicates the growing momentum of the civilian UAS market. The release of UAS guidelines by the DOJ follows the FAA’s notice of proposed rulemaking (NPRM) with respect to non-recreational sUAS operations, which was released in March of this year. The NPRM details daytime flight, altitude, operator certification, and line of sight restrictions under consideration by the FAA. Pending the implementation of domestic UAS regulations, the domestic UAS market will comprise an increasing share of the global civilian UAS market growth of nearly $100 billion over the next decade. The market for law enforcement UAS will provide significant opportunities for firms with experience providing sUAS systems to the US Military, such as AeroVironment, which produces the the “Wasp,” “Raven,” and “Puma” (Finnegan, 2013).
Sources
- Department of Justice Policy Guidance 1 Domestic Use of Unmanned Aircraft Systems (UAS), 2015
http://thehill.com/sites/default/files/dojdronememo.pdf - DOJ lays down some privacy rules for feds flying drones, Mariella Moon, 2015.
http://www.engadget.com/2015/05/23/doj-drone-privacy/ - Game of drones: As U.S. dithers, rivals get a head start, Jeremy Wagstaff, 2015.
http://www.reuters.com/article/2015/03/08/us-tech-drones-idUSKBN0M40VM20150308 - Justice Department releases guidelines on domestic drone use, Dante D'Orazio, 2015.
http://www.theverge.com/2015/5/23/8650459/justice-department-domestic-drone-guidelines-published - Public safety market offers growth for UAVs, Philip Finnegan, 2013.
http://www.aerospaceamerica.org/documents/aerospaceamerica-pdfs-2013/march-2013/aa-industryinsights_mar2013.pdf

Office of Personnel Management
The Office of Personal Management (OPM) is the victim of a highly intrusive cyber espionage operation conducted by “Deep Panda”, a state backed Chinese hacker group. The personal information of over 4 million current and former government employees dating back to 1985 has been compromised. Chinese hackers managed to circumvent the much vaunted EINSTEIN 3 cyber intrusion monitoring and blocking system (Sternstein, 2015). Once OPM’s network was penetrated, the hackers were easily able to access government records, as OPM’s personnel data was unencrypted (Perera, 2015). The breach was initially discovered by CyTech Services, which ran diagnostic software of OPM’s network in a sales demonstration in April of 2015.
Several US intelligence officials stated that the collection of OPM personnel records represents a goldmine for Chinese counterintelligence activities. In tandem with the Anthem Inc. and Premera Blue Cross breaches conducted by Deep Panda, the Chinese government has the medical records, security clearance statuses, social security numbers, performance ratings, addresses, and other compromising personal data of millions of US government employees (Barrett, 2015). The data is useful in both the recruitment of Americans by Chinese intelligence services and identification of American spies within the Chinese government.
Cyber security experts have been widely critical of OPM’s failure to safeguard its networks given the sensitivity and volume of its personnel files. Adam Firestone, Senior Vice President and General Manager of Kaspersky’s Government Security Group, remarked that the government needs to reassess its approach to cyber security from “perimeter defense” to the internal defense of networks:
“The issue is how the network was prepared for the breach. And what were the internal security mechanisms inside the network to prevent the information inside the network from being used and useful for an adversary who got in. From our perspective we assume a breach, we assume that everything is porous, but we prepare. The idea is to prepare the network and your systems for the breach such that even though they do get in, what they retrieve is not useful.”
Navy Cyber Command has demonstrated the viability of this approach as it has managed to fend off every cyber intrusion since the Navy-Marine Corps Intranet breach in 2013. Cyber Fleet Commander Vice Admiral Jan Tighe attributed the success of Navy Cyber Command to the prompt internal defense of its networks, noting that initial breaches were inevitable. It is unclear how the United States will respond to China given the Department of Defense’s newly released cyber strategy which emphasizes the US will retaliate against cyber-attacks (Stewart, 2015). The distinction in the OPM case is the hacker group did not destroy OPM networks or hardware, but committed an act of espionage.
Sources
- Chinese hackers may have breached the federal government’s personnel office, U.S. officials say, Fred Barbash and Ellen Nakashima, 2015.
http://www.washingtonpost.com/news/morning-mix/wp/2014/07/09/report-chinese-hacked-into-the-federal-governments-personnel-office/ - Navy, Marine Cyber Fought Off All Net Attackers Since 2013, Sydney J. Freedberg, Jr.,2015.
http://breakingdefense.com/2015/05/navy-marine-networks-have-defeated-all-attacks-since-2013-cyber-admiral/ - Anthem Breach May Have Started in April 2014, Brian Krebs, 2015.
http://krebsonsecurity.com/tag/crowdstrike/ - The Chinese Have Your Numbers, 2015.
http://www.wsj.com/articles/the-chinese-have-your-numbers-1433716388 - U.S. Weighs Extent of Suspected Data Breach by Hackers in China, Devlin Barrett, 2015.
http://www.wsj.com/articles/u-s-weighing-extent-of-suspected-data-breach-by-hackers-in-china-1433537206 - U.S. Suspects Hackers in China Breached About 4 Million People’s Records, Officials Say, Devlin Barrett, Danny Yadron and Damian Paletta, 2015.
http://www.wsj.com/articles/u-s-suspects-hackers-in-china-behind-government-data-breach-sources-say-1433451888 - Opm Hackers Skirted Cutting-Edge Intrusion Detection System, Official Says, Aliya Sternstein, 2015.
http://www.nextgov.com/cybersecurity/2015/06/opm-hackers-skirted-cutting-edge-interior-intrusion-detection-official-says/114649/?oref=ng-HPtopstory - China's Cyber Attack, Defense News, 2015.
http://www.defensenews.com/videos/defense-news/2015/06/09/28644395/ - U.S. Spy Agencies Join Probe of Personnel-Records Theft, Damian Paletta, 2015.
http://www.wsj.com/articles/u-s-spy-agencies-join-probe-of-personnel-records-theft-1433936969 - Pentagon's new cyber strategy cites U.S. ability to retaliate, Phil Stewart, 2015.
http://www.reuters.com/article/2015/04/23/us-usa-pentagon-cyber-idUSKBN0NE0AS20150423

Motorola HC1 Headset Computer
Wearable technology, devices that are worn by users, is a rapidly expanding market which is set to exceed $32 billion by 2019 (IHS, 2014). Commercial wearable technology applications include biometric monitoring, camera and video functions, communication systems, and internet access. Many of these functions could be expanded upon to assist law enforcement by providing greater situational awareness to both officers and dispatchers. Furthermore, the use of body mounted cameras provides an additional means of ensuring accountability among law enforcement personnel, as per the Obama Administration initiative to field more than 50,000 police body cameras nationwide.
The most relevant capability of wearable technologies to law enforcement relate to increased situational awareness functions. For example, biometric sensors would be able to alert dispatchers of a potential emergency situation. Datalinks would enable officers to rapidly exchange information between networked officers and dispatchers including video feeds from body cameras, maps, floor plans, and data from platforms such as unmanned aerial vehicles. Wolf Tombe, Chief Technology Officer of U.S. Customs and Border Protection, it is examining fielding a wrist mounted drone:
“[CBP] is considering are small unmanned aircraft, including a drone mounted on the wrist. Such technology would meet CBP new technology requirements: enhancing officer safety, increasing mission effectiveness — and reducing costs, he said. If it does any or all of those things, ‘bring it in and we’ll look at it’ - John M. Doyle, 2015
Interest in wearable technologies extends across multiple DHS agencies including the Science and Technology Directorate (S&T) directorate. S&T recently launched “Emerge Accelerating Wearable Tech for First Responders,” a $750,000 program to develop wearable technologies to improve the situational awareness of first responders.
The Obama Administration is seeking to acquire wearable body mounted cameras for nonfederal law enforcement officers as a means of improving accountability between the police force and citizens. In response to the Ferguson Missouri riot following the death of Michael Brown, the Obama Administration announced the planned acquisition of 50,000 body cameras for officers nationwide. A total of $20 million in grants has been allocated towards purchasing police body cameras with a total of $75 million expected over the next three years pending Congressional approval (Edwards, 2015).
Despite the substantial capabilities and potential of wearable technologies for law enforcement, significant barriers remain towards the widespread proliferation of wearable technology in law enforcement. Alternative existing equipment, such as mobile devices, could provide some of the situational awareness and data sharing capabilities at greatly reduced cost over proposed wearable systems. Relatively simple body cameras and biometric sensors will likely see expanded use over the next few years. However, until the cost of wearable computers and wearable UAS drops substantially, wearable technologies will not meet their full potential given the limited deployment of more expensive high-end wearable systems.
Sources
- Improving Our View of the World: Police and Augmented Reality Technology, Thomas J. Cowper & Michael E. Buerger, 2003.
https://www.fbi.gov/stats-services/publications/police-augmented-reality-technology-pdf - A Guide to the $32b Wearables Market, HIS Janes, 2014.
https://technology.ihs.com/515418 - RoboCop: Wearable Tech, Melanie Basich, 2015.
http://www.policemag.com/channel/technology/articles/2015/04/robocop-wearable-tech.aspx - FACT SHEET: Strengthening Community Policing, Office of the Press Secretary, 2014.
https://www.whitehouse.gov/the-press-office/2014/12/01/fact-sheet-strengthening-community-policing - 5 wearable tech trends for police, Mary Rose Roberts, 2014.
http://www.policeone.com/police-products/communications/articles/6989352-5-wearable-tech-trends-for-police/ - The Future of Wearable Technologies in Law Enforcement, Sean Petty, 2014.
http://www.lawofficer.com/articles/print/volume-10/issue-6/leadership/future-wearable-technologies-l.html - HOMELAND SECURITY: Customs and Border Protection Exploring Small Drone Use, John M. Doyle, 2015.
https://4gwar.wordpress.com/2015/02/26/homeland-security-customs-and-border-protection-exploring-small-drone-use/